Merkle filesystems are a type of block-level validated filesystem, providing integrity protection when they are used in a secure boot environment. QNX recommends that you replace Merkle filesystems with QNX Trusted Disk.
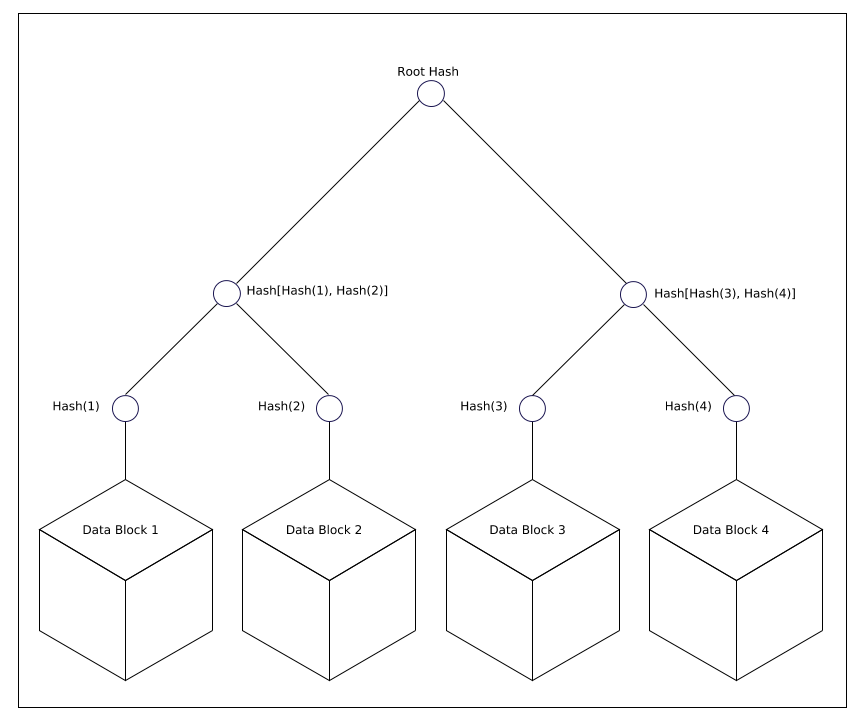
Figure 1. Hash values are created from data blocks
The Merkle filesystem filter is supported by the fsf-merkle.so shared object.
The Merkle driver sits between the raw block device and the upper filesystem layer that is supported (for example, the Power-Safe filesystem, fs-qnx6.so). It verifies the integrity of the data upon read access, using the hash tree metadata, before allowing it to be returned to the requester. In case of a verification failure, an error is returned instead. Merkle filesystems are read-only.
The Merkle hash tree metadata is signed and verified using a key pair. Verifying the signature ensures that the root hash of the tree is valid and hasn't been tampered with. It is the root of the trusted verification mechanism.
The size of the Merkle filesystem image depends on the underlying filesystem block geometry as well as the chosen digest algorithm. The mkmerklefs utility can be used to generate statistics of how much extra space is consumed by the metadata.
Secure hash algorithms
Merkle filesystems support the following secure hash algorithms: sha256, sha512.
Signing keys
Signing keys need to be generated as a 2048-bit RSA public/private key pair in PEM format. You can generate a 2048-bit RSA key pair with the following commands:
openssl genrsa -out private_key.pem 2048 openssl rsa -pubout -in private_key.pem -out public_key.pem
Crypto engines
OpenSSL is the only crypto engine supported by Merkle filesystems on QNX.